Vulnhub: InfoSec Prep: OSCP
Posted on 10 Aug 2020 in security • Tagged with security, boot2root, vulnhub, Linux, lxd, lxc • 4 min read
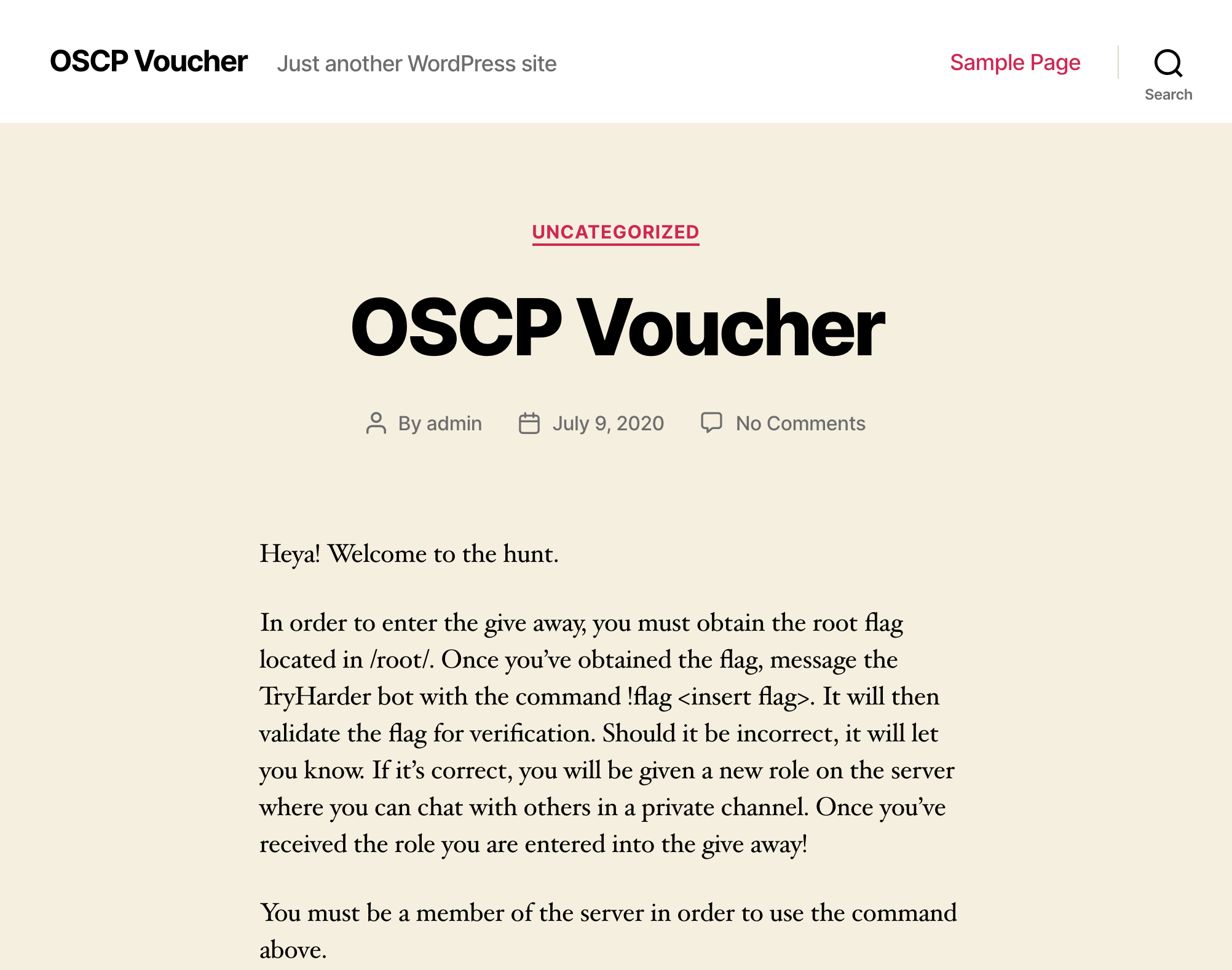
This is a writeup about a vulnhub machine
InfoSec Prep
This box is an really easy box in order to make a small selection for entering a
give away for a 30d voucher to the OSCP Lab, Lab materials, and an exam attempt.
The box was created by
FalconSpy and publish on July
11 2020.
It involves a robots.txt file, some base64 an SSH key, lxd and a SUID binary.
Continue reading
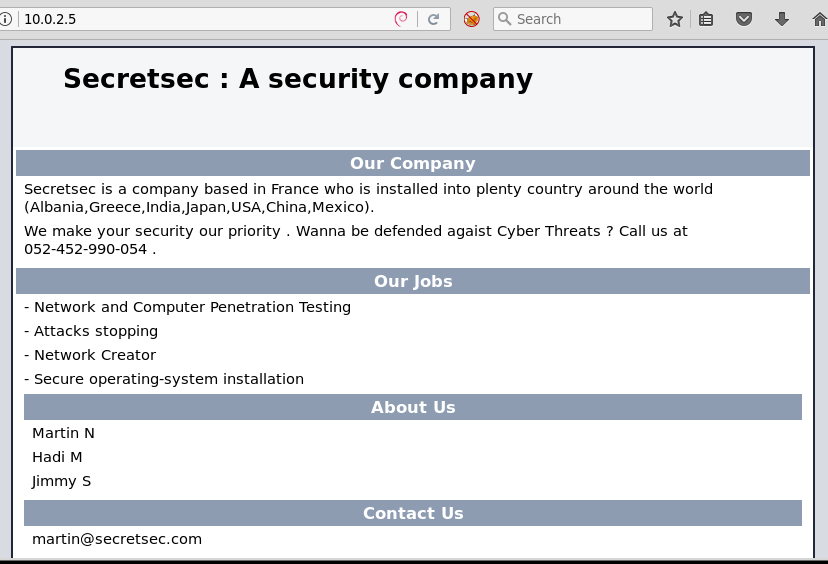
 A few days ago, I installed a new pentesting box based on Arch Linux with Kali
A few days ago, I installed a new pentesting box based on Arch Linux with Kali